Understanding Card Not Present Transactions & Security
Alright, here’s a little test to kick off your day. Take a look at the following picture.
When keying in card not present transactions, this picture is proof of a secure transaction. True or false?
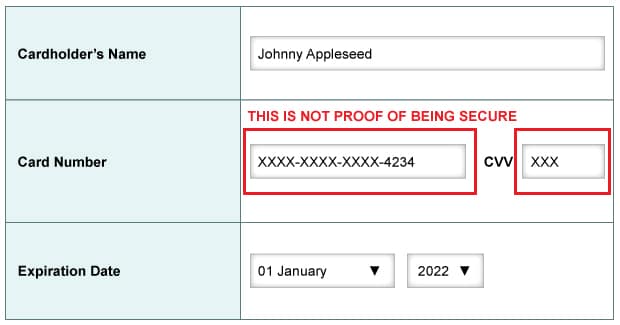
Did you answer true? It looks secure, right? The credit card number is XXXed out, and that means a hacker can’t steal anything, right? Wrong! The answer is FALSE. Nothing about this image proves the transaction is secure.
Okay, so some of you may have answered false (congratulations, you had a 50/50 shot). But let’s kick it up a notch. Why is the answer false? What common assumption about this picture doesn’t indicate security?
The answer is false because hidden card information is NOT proof of being secure!
We’re often surprised at how prevalent this thought process is among the merchants we speak to. A lot of merchants assume that if a virtual terminal “hides” the credit card and CVV number, they are securely entering in the payment information. Unfortunately, this is completely not true. About the only thing this is preventing is if a hacker were to be standing directly behind you and copying the card number while you type it. And we’re pretty sure you’d notice that due to the creepy, hot breath on your neck.
So Where’s the Problem?
The problem here isn’t what you are seeing. It’s what you can’t see, and you can’t see what is happening on your network. In today’s age of digital threats such as malware and network breaches, you have no idea who’s taking a peek at what you are doing from the other side of the internet.
Malware and spyware such as keylogger programs can actually monitor your keystrokes as you type. So while you may not visually see what is being typed, it’s possible malicious software is stealing the data.
P2PE to the Rescue
But don’t fret! There are security tools available to stop this from happening. This is where P2PE (point-to-point encryption) and devices such as the SecureKeyTM M130 come in.
P2PE includes all the things that are designed to protect your secure credit card transactions and includes software, applications and devices. P2PE will encrypt the data you transmit so that malicious programs won’t be able to run off with the information. Most often, P2PE is used when you swipe a card so that the data contained within the magnetic strip is encrypted, making it useless to hackers. Enabling P2PE is also makes becoming PCI-DSS compliance easier.
That’s great you say, but this sounds like it’s just protecting card swipes. What about card not present transactions like mentioned above? Good catch! P2PE also protects those transactions as well, but for additional security we recommend using a device such as the SecureKeyTM M130. This is a device that plugs into your computer and looks very similar to an extra number pad from you keyboard. Some models have an additional card swipe reader, but the benefit we’re focusing on is that the keypad further encrypts your keystrokes and leaves nothing that a hacker can access.
Tying it all Together
There you have it. Just because the card information is obscured on your monitor, it doesn’t necessarily mean you are securely transmitting the data. To truly be secure, you need to have P2PE and an encrypted keypad in order to protect sensitive card data. As an added benefit, we accept a reduced PCI compliance regimen if this is your only type of credit card acceptance. Also, you can further secure your organization’s data by coupling P2PE along with the Advanced Security Package to ensure a secure environment. If you have additional questions or would like to inquire about getting this set-up on your account, please contact us.
[su_button url=”/contact” background=”#5a6e16″ size=”10″ center=”yes”]CONTACT US[/su_button]